Generally, we Internet,It is to plug the Internet cable,Dial need at most。However, in the enterprise network application environment may have more complex,This is a general home network can not understand。so,Acting this feature came into being。
Agent name suggests is your place to visit you can not access resources。
Defined on Wikipedia is this:
Agent (English:Proxy),Also known as the Network Agent,It is a special network services,Allows a network terminal (typically client) through this service with another network terminal (typically a server) non-direct connection。Some gateways、Routers and other network equipment with network proxy。Generally considered a proxy service will help protect the privacy or security of the network terminal,Prevent attacks。
Among the proxy,Agents will generally be divided into three,That forward proxy、There is a reverse proxy transparent proxy。Then,We turn these agents 818。
Forward Proxy
Forward proxy is our greatest exposure to the agent mode,usually,Many companies previously (now there are many) employees are not allowed to access the network easily,Some are part of the external network,If you want or need to access network resources,Then you will probably want to set up a proxy server of your own home。This time you will find,Forward Acting general are C / S architecture,It is through the client,You will want to access a station's request package,Then sent to a proxy server,The proxy server is responsible for sending your request to the destination station。- In this way,You can bypass the firewall shield。
Other,If you want to access a stand quietly,I do not want to let others know,You can also use a proxy,Through highly anonymous proxy access,So you trail was completely hidden,Others will find access to the information of the proxy server instead of your,So as to achieve the purpose of hiding the traces。
Due to the different needs of,Certainly spawned a number of agents for different purposes,For example, our most common HTTP proxy、FTP proxy、SSL proxy, etc., etc.。
Oh, right,There are more low-level proxy socks,This special number,It does not care what your agent agreement,It will all take the line and your IP packets,but,Although we often use sock5 proxy shadowsocks,However, support for UDP is not perfect。(Already supports UDP,But in the last of the DNS so that,Otherwise unclear。)
Forward Proxy will be distinguished according to whether or not a high degree of anonymity:
Highly anonymous proxy
Such a server will your packets forwarded intact,As if their own;So in terms of the target station,Simply you will think that is a proxy server to access it instead of you;
Ordinary anonymous proxy
In terms of height with respect to anonymous proxy,Such a server would be recognized destination station is a proxy server,Thus probably still track your real IP。
Transparent Proxy
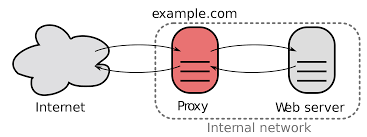
In fact, this can not be positive、Reverse Proxy tied,Because it is in a forward proxy;It does not encrypt your information,But clear enough to tell you the target station is accessed through a proxy! Of course, the benefits are allowed to cache,And some rules to make your visit safer - transparent proxy typical application is the network hardware firewall。(but,We often say shadowsocks transparent proxy with this definition different,The former represents the relative computer access,Agent is transparent;The latter represents the relative target site,Agent is transparent。)
Reverse Proxy
Having a forward proxy,Let 818 as opposed to the reverse proxy,With respect to the forward proxy is,Reverse proxy technology content higher,And more extensive range of applications,Small to you proxy access website ,Large internal load balancing to the site will use this technology to。
Actually, the most typical application of this technology is in the back-end services,For example, a large site with a server,Then the back-end server is responsible for the calculation of N units,In fact, the real server on this server N,This N server via some mechanism to synchronize content,Then the front of the server is only responsible for sending and receiving data,Then the front end after receiving the request will be based on a back-end server resources free to decide to whom the request reverse proxy,So as to achieve the purpose of load balancing。
For example, before the general rate Taobao,Later that revolutionized the load balancing system,For this process requires a reverse proxy agent,Taobao this proxy process halved,That is above the N servers in a front-end station after receiving the request will not return data to the front end,But direct feedback to the user。(In this specific case forgotten,Two years ago a friend told me to listen ...... seeking treatise。)
Anyway,Later, it was the reverse proxy to play the bad people,From building the cache server,To phishing attacks,Then later become our common ladder ......
It is characterized by the absolute protection agent can be something behind,Users can only access to the proxy server,And what happens behind the proxy server you will never know,Such an action would make it very dangerous,This is definitely a black box。For example, for fishing,Quietly tampering with your access links and the like,No problem。so,If you want to use a reverse proxy ladder,We must find absolutely trust services provided by - or simply a build-it-yourself only to the people around him with。
Reverse proxy to talk about it so much,It is generally used in a multi-developer environment,Anti behalf of a domain name is the most important feature a station,For example, we often those cross-border anti-Google Generation,Google is obviously accessible,However, the domain name is not the same Jiang Zi。In fact, you also visit Taobao Jingdong ah ah are anti-Generation Site,Just more technology,And they just stand their own anti-Generation ha ha!
Transparent Proxy
Front spoken,Transparent Proxy This should be a forward proxy branch level,But why would it still be willful separately carry out eight hundred eighteen of it? As mentioned above,This either-transparent proxy transparent proxy!
We are here to transparent proxy,Especially where we had a variety of small household router proxy,Thus,To achieve a normal Internet computer but actually being out of the effect of the agent - the computer is relatively transparent proxy。
Thus,It is imperative to include incoming VPN,Speaking VPN it actually does not belong to the agent,Simply, one is that they have been developed out of the mind is not the same,So to speak,your home,Firewall,the company。Three places,Although the means and VPN agents are to penetrate this wall,But the purpose of the agent is out of the company,The VPN is connected to the company from home。So the agent only forwards some corresponding data packet,The VPN is logically make your computer "through" to the destination,In order to achieve the Internet there。
but,It is not important for our "transparent proxy" is concerned,Using a transparent proxy on the router,There are two general,One is to use socks5,For example shadowsocks;Another is vpn ;Through a special router,Allow them to implement proxy,Internet data packets so that you will be issued a proxy router "Auto" to。
You see,Relative to your computer,your phone,Your iPad in terms of,This agent is not to become "transparent" of it?
Further reading:
Detailed forward proxy Proxy Reverse Proxy
http://zh.wikipedia.org/wiki/代理服务器
Original article written by LogStudio:R0uter's Blog » On the forward proxy reverse proxy transparent proxy
Reproduced Please keep the source and description link:https://www.logcg.com/archives/929.html
Or some of these things away for ordinary Internet users。
This is indeed a very troublesome problem indeed! How to make people aware that they have been blocked out? After all, for most people,Internet is only the QQ and microblogging microblogging and everyone had ......,Who needs Twitter and Facebook,I think I gave thanks to the "success" of the English class system。