Before I wrote an article,Use fail2ban Bind9 be used to prevent DNS amplification attacks,Never imagined,original WordPress It can also be used for amplification attacks,The principle is its Pingback mechanism。
Pingback is a tool for mutual notification between WordPress websites,For example, A blog refers to a link to a B blog post,Then WordPress can automatically help you notify B blog,Tell the blogger that you quoted his article。
This was originally a very good feature,But one thing-Wordpress has not done a security check for this Pingback。Wordpress will detect whether the source station is valid when it receives Pingback-this needs to communicate with the source station,But it does not detect whether the ip sent from pingback and pingback are the same ...
That is,Send tens of thousands of pingbacks containing the IP of another website to 100 WordPress,Then it can be amplified to 1 million TCP connections to that website by reflection!
This is not DDoS What 0.0
so,Still close it ...
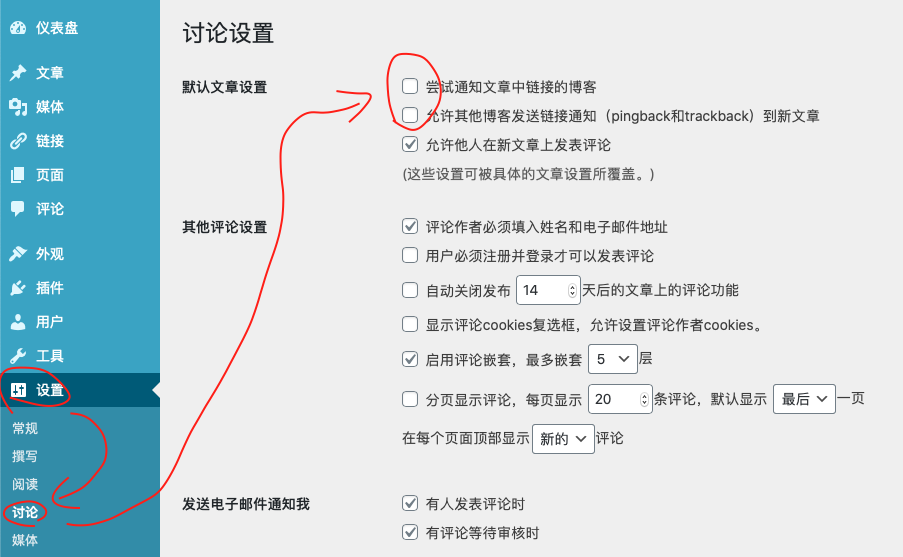
Turn off Pingback and Trackback
Since this is closed,So if you do n’t need XML RPC for WordPress,Close it together。This RPC is used to call WordPress remotely for users,For example, a client ... If you use it,Never mind。
Close WordPress XML-RPC service
This service was actually vulnerable in the early days,Later until now,Actually XML-RPC Service vulnerabilities have already been fixed (surprisingly Pingback The loopholes have remained-for so many years ...)
In your theme's functions.php,Add the following statement to close:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 |
// 彻底关闭已经发布的文章的pingback 和 trackback add_filter( 'wp_headers', 'pmg_pk_filter_headers', 10, 1 ); function pmg_pk_filter_headers( $headers ) { if( isset( $headers['X-Pingback'] ) ) { unset( $headers['X-Pingback'] ); } return $headers; } add_filter( 'rewrite_rules_array', 'pmg_pk_filter_rewrites' ); function pmg_pk_filter_rewrites( $rules ) { foreach( $rules as $rule => $rewrite ) { if( preg_match( '/trackback\/\?\$$/i', $rule ) ) { unset( $rules[$rule] ); } } return $rules; } add_filter( 'bloginfo_url', 'pmg_pk_kill_pingback_url', 10, 2 ); function pmg_pk_kill_pingback_url( $output, $show ) { if( $show == 'pingback_url' ) { $output = ''; } return $output; } add_filter( 'pre_update_default_ping_status', '__return_false' ); add_filter( 'pre_option_default_ping_status', '__return_zero' ); add_filter( 'pre_update_default_pingback_flag', '__return_false' ); add_filter( 'pre_option_default_pingback_flag', '__return_zero' ); add_action( 'xmlrpc_call', 'pmg_pk_kill_xmlrpc' ); function pmg_pk_kill_xmlrpc( $action ) { if( 'pingback.ping' === $action ) { wp_die( __( 'Pingbacks are not supported' ), __( 'Not Allowed!' ), array( 'response' => 403 ) ); } } register_activation_hook( __FILE__ , 'flush_rewrite_rules' ); register_deactivation_hook( __FILE__, 'flush_rewrite_rules' ); /* 关闭 xml rpc 避免漏洞 */ add_filter('xmlrpc_enabled', '__return_false'); |
Prohibit access to xmlrpc.php
If you use Nginx service,Then add in your nginx site configuration
|
1 2 3 |
location /xmlrpc.php { deny all; } |
This completely prohibits external access to this file。
postscript
If it were not for someone to come to your door and say that my blog was used to reflect amplification attacks against other websites,I really do n’t know that the security vulnerability of WordPress four or five years ago has not been fixed until now ... To be honest, this function is quite easy to use,Because of it,I caught a few guys who carelessly stole my article and pretended to be original ... 😂
Some friends also said,Disable this feature without patching this vulnerability,It ’s like a doctor treating a patient by killing a patient ... that ’s right,But considering that every WordPress update and upgrade may overwrite this file (and not necessarily fix this vulnerability),And usually I don't use this function,Just close it。
Reference links
- O hai let me wanna-be!
- WordPress tips:Disable XML-RPC service
- A large number of WordPress sites are penetrated ,Become a source of DDOS attacks
Original article written by LogStudio:R0uter's Blog » Avoid WordPress being used as a reflection amplification attack
Reproduced Please keep the source and description link:https://www.logcg.com/archives/3351.html
Hi, original author here. I am sorry I do not understand Chinese ; however of what I understand you are advising turning off the WordPress trackback mechanism altogether ?
This is not such a good idea in general, it seems to me like a doctor shooting the pacient to treat him. Instead of taking radical measures, there is a simple fix discussed in the article : simply check that the caller of xmlrpc uses the same IP as the website reported for trackback. This sterilizes the discussed avenue for amplification.
…you are right, but I am not sure if xmlrpc.php changed back when WordPress updated, that’s why I turning this off instead.
🙁