I remember someone saying:
We, as an ordinary person,Money is not state apparatus more,No country strong force machine - but on cryptography,It may be the first individual to an equal footing with such huge machine。
Internet all the time filled with a variety of information,Every word we uttered,Like every point,They are the equivalent of saying to everyone listening,it's here,Every word we can spread very far,Our every move,Potentially seen by anyone。This is different in our daily life。Our lives are visible and tangible,Is perception and control。You speak,Many heard,Instead,Says little,Fewer people heard。You can see and your people expression,Be able to hear their voices。But networks,A lot of people treat it with reality – a famous Terrier (the virtual nature of the Internet):
You never know at the other end of network,Talking to you is a dog。
privacy
How to protect your privacy on the Internet? In recent years, people are finally beginning to realize that this problem,Unfortunately most of the people still speak:“I have nothing to hide"--It's not to hide anything--just to make your life the same as before,Make what you say,And you are in real life--onlyPeople who need to see see。
But such a simple requirement,On the Internet has become the most difficult proposition--which is another feature of Internet:Resource sharing。
So,On the Internet,By default, everything isOpenof,Data is public! Anyone who is willing to,You can easily visit you on to do everything。
--Do you like without clothes to go out every day?
Cryptography
So,We need to take some measures to protect their。What you say--not necessarily secret,But we don't want to let it be heard all。Reality you sound due to loss of energy eventually dissipates to nothing,Even be heard,Also over time forgotten。In the Internet,These are information,Information can be permanently saved。
Your keyboard will faithfully record all your。
What years fight hot: cloud storage? You know thatHigh availabilityIs one of its key characteristics? All right,This is a technical term,But that's okay,Very simple,Means highly available。In the previous,Our online documents are saved,Is saved to a remote server。Once you have deleted or the server is offline,Your document is gone forever。
Now,Your online documents,Then into a bunch of server clusters,Even,May be clusters of clusters of servers around the world--no one knows you exist which document the physical hard drive--or,Which hard copies of this document are you--because no matter which server is broken or off line,Your document can be accessed after all – even if you've deleted--what makes you so sure you really delete it? Just put your own document to shut down。
So,We need to use cryptography tools,Back for the second best,Documents that cannot be destroyed in the future can only be read by a person designated to。
Symmetric encryption
We say encryption,That encryption what is a thing? For direct,Is with a "lock",Lock up your documents,People and then send you the keys allow you to open。
of course,We use a special mathematical formula to calculate the zero and one,The result is the key,it's here,Our professional translation--Key。
This is called it "month" or "to be",Your mood,Because it is a polyphonic:)
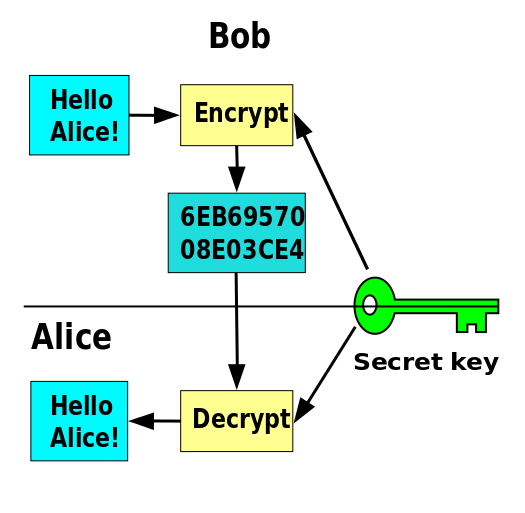
Speaking of encryption,I have to mention Alice and Bob The pair,HA HA – who are they? Grace,Just like English classMing LiandHan meimei~ ~
You see,Our Bob sends Alice a message says"Hello Alice! ”,But he did not want to let the whole world know this thing right? I had him on the content of the message encrypted,So what others see is garbled。And then Alice got a message,And Bob agreed key to decrypt,And then she got"Hello Alice! ”--The contents of the entire process,Only Alice and Bob will know that a message of real content,While others,Such as mail forwarding,And people who steal mail,Can not see the。
Do you know? Every day in the sent mail,In fact is not the least bit encryption,Anyone can easily get a copy of your message。You cannot delete messages,Do you think they are all deleted,In fact, server administrators can easily find your account and all messages! They are marked as "deleted" and no longer shows you!
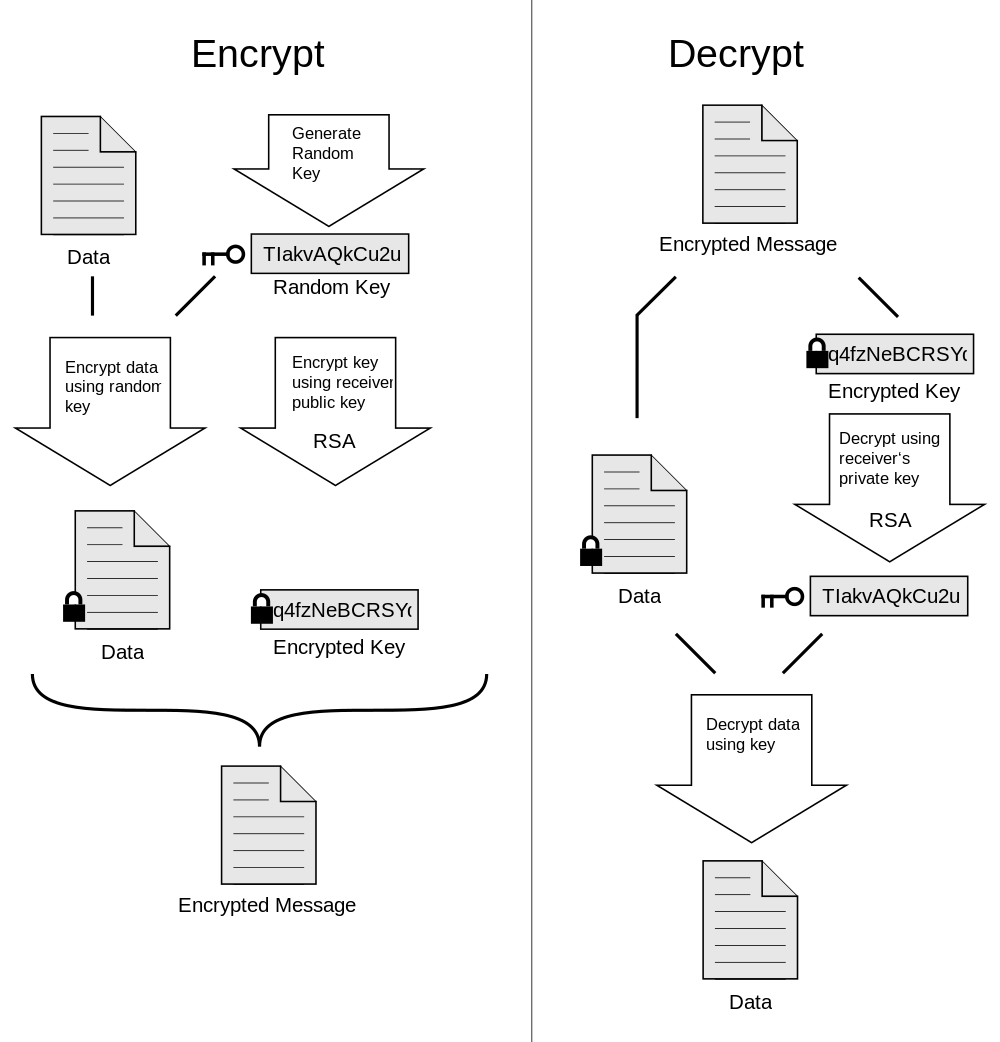
But there is a problem,If anyone gets my keys also can do unlock my messages? Well, Bob must have came up with this thing,If two lines meet to say,Direct copying of keys just fine--but if it is from far away,From the Internet to pass key,So it wouldn't be safe, right? So,There is another way to encrypt:
Public key (asymmetric) encryption
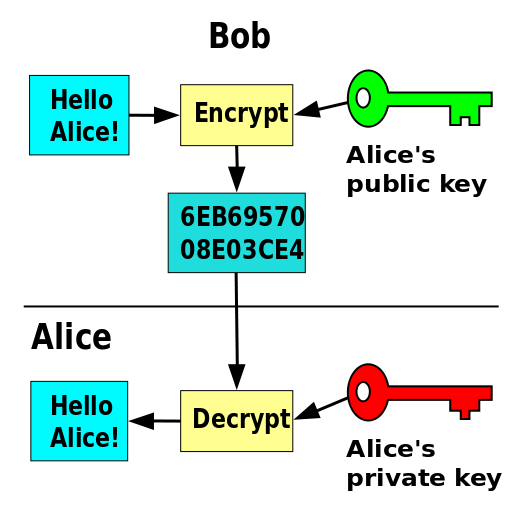
Bob updated the algorithm,Our mathematical formulas have two solutions--one can only compute the encrypted content,And the other only to decrypt the encrypted content。Such,We just need encryption key can only be handed out now,Others even get the public key,He can only be encrypted and cannot be decrypted!
You see,Bob informed Alice that he has to send Alice an email,All bad guys squint eye。Then Alice sent to Bob a public key,All of the bad guys got it。Bob use public key encrypted message to Alice ,This process millions of people to get a copy of this email,They have been key to decrypt the message-failure。
Alice keep the private key used to decrypt the message,Haha,Only she knows。
note,Our approach to information theft and theft is also different in real life。You have 100 dollars,I stole it,You would not;And for information,In particular electronic information,I stole a,Your information--you didn't even know it was stolen! This is the purpose of social engineering,Here we start with technical means。
Then,This technique is called what?
PGP(Pretty Good Privacy)
This encryption initially is open source because it is so cool and so cause a chain of events,So it was open source and the software was set up in 1996 the company。Now,We generally use PGP Instead of calling this company。
but,Because the encryption is so important,It has been sweeping the world,So people began to consider the development of a can and it is compatible and complimentary solutions。
But this is too confusing,Final,Submitted to the IETF PGP PGP 5 Standard,then IETF Man thinking,Feel good,Get a OpenPGP This standard out。Such,We can develop software to perfectly compatible with PGP Now。
GnuPG(GNU Privacy Guard)
so,Free Software Foundation developed the GPG,It is fully based on the OpenPGP standard,With the PGP Universal and it's free!
Here we talk about,How on a Mac
Protect your privacy
GPGTools
Says,If you directly use GnuPG You may actually,But it does not have a graphical interface,I think using the command line you must master is not a difficult-but,After all the trouble--after all,,With GUI Related things,We still use the GUI tools to solve it is more appropriate to。
so,We use a dedicated package management tool for OS x GPGTools,It can help you graphically using GnuPG,Also help you fix upgrade problem,One-click installation, Yo ~
All right,We now have to download it:https://gpgtools.org
This is a OSX application encryption suite,Inside contains a:
- The GPG plugin with the Apple Mail app--I recommend you useThunderBird mail clientInstead of the,This better enables,Better support for GPG;
- A graphic end of GPG-management tool;
- To your computer to install GPG services,So you can use it on almost any software;
- Of course GnuPG command line,So you can use it。
Configuration
We open the GPG Keychain This application,Then turn it,This is our managing graphics port。
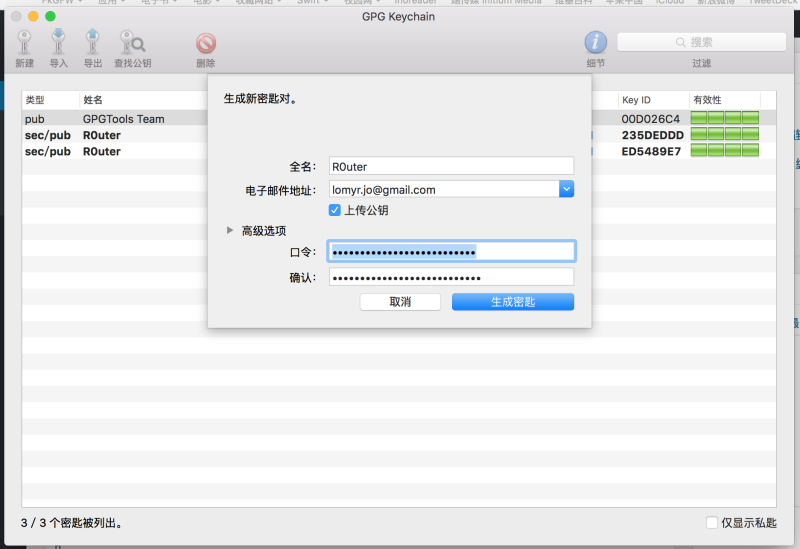
Click on the upper left corner to create a new key:
Here it is automatically read from the messages you add mailbox,If there is no,Then you need to write in。The first line is, of course, your name。Then the password,This password is used to protect your private key! When you need to decrypt a document when,To the private key is used, right? Will prompt you with the private key to decrypt!
Then that "Upload public key”,What does it mean? Is that it will automatically upload your public key to the key server--after all,,Key the thing has 4096 Bit length,You directly to the public may be very troublesome,So you can search directly through the email address here! Now you can try to search my email:)
For advanced settings,It doesn't matter,Because the default is the strongest。But your key has a shelf-life,Expired-cancelled,Avoiding it will be always be used ~ the default is five years。
Then build,Build process can be a little long,It requires calculating a large number of random numbers,When you move the mouse to browse the Web page,This can help it compute faster (in theory,As well as more random)。
Once you have completed,Have your keys Ready to use!
Advanced Configuration
edit ~/.gnupg/gpg.conf ,At the end of the file (if there is no file is created) to comment out lines that already exist,Then add the below content:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
auto-key-locate keyserver keyserver hkps://hkps.pool.sks-keyservers.net keyserver-options no-honor-keyserver-url keyserver-options ca-cert-file=/etc/sks-keyservers.netCA.pem keyserver-options no-honor-keyserver-url keyserver-options debug keyserver-options verbose personal-cipher-preferences AES256 AES192 AES CAST5 personal-digest-preferences SHA512 SHA384 SHA256 SHA224 default-preference-list SHA512 SHA384 SHA256 SHA224 AES256 AES192 AES CAST5 ZLIB BZIP2 ZIP Uncompressed cert-digest-algo SHA512 s2k-digest-algo SHA512 charset utf-8 fixed-list-mode no-comments no-emit-version keyid-format 0xlong list-options show-uid-validity verify-options show-uid-validity with-fingerprint |
At last,, Use the following command to add a certificate to the Keyserver to make it use the Https request certificate:
|
1 2 |
$ curl -O https://sks-keyservers.net/sks-keyservers.netCA.pem $ sudo mv sks-keyservers.netCA.pem /etc |
use
First of all go to System Preferences → Keyboard→ Shortcut keys → service Check all options on OpenPGP。
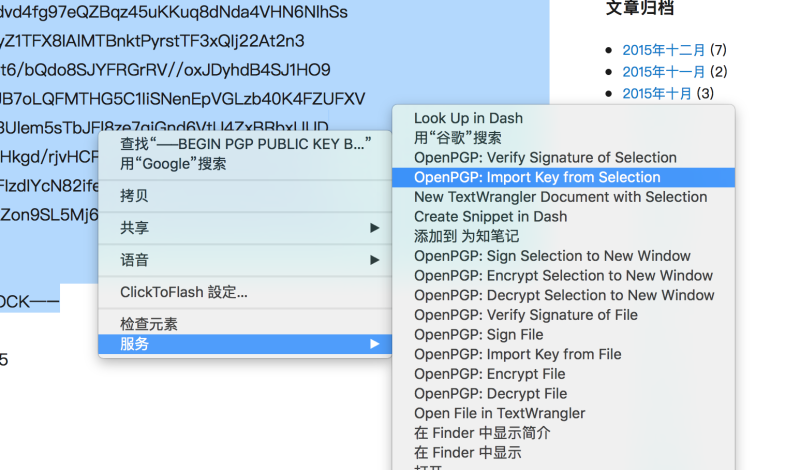
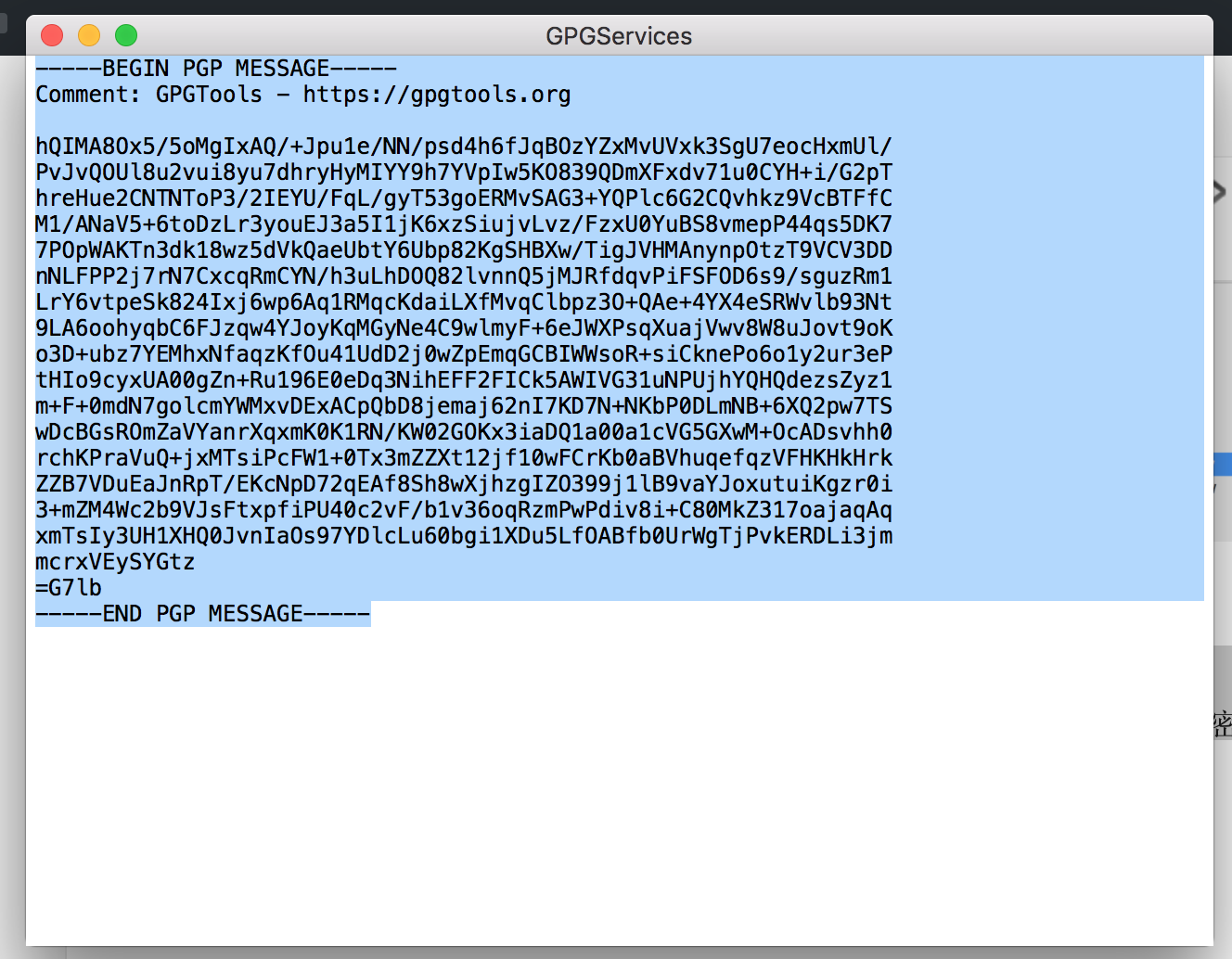
then,You can give it a try,ToThis page,Select all characters,Included —–BEGIN PGP PUBLIC KEY BLOCK—– and —–END PGP PUBLIC KEY BLOCK—– This two-line comments, Oh! Then right click,Select the bottom of the service And then the second-level menu, select OpenPGP: Import Key from Selection
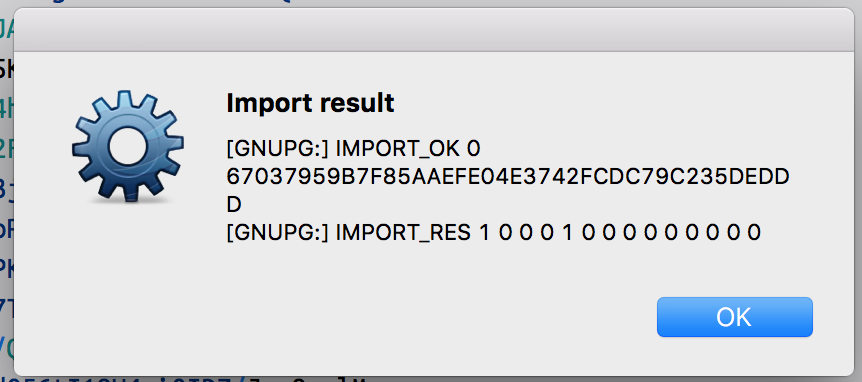
If all things go well,You should see the dialog box that is similar to the following:
or,You can also search directly in the GPG Keychain my email address lomyr.jo@gmail.with ,If you see multiple results,You try to import the latest。
This time,You can send me encrypted content! How to encrypt it?
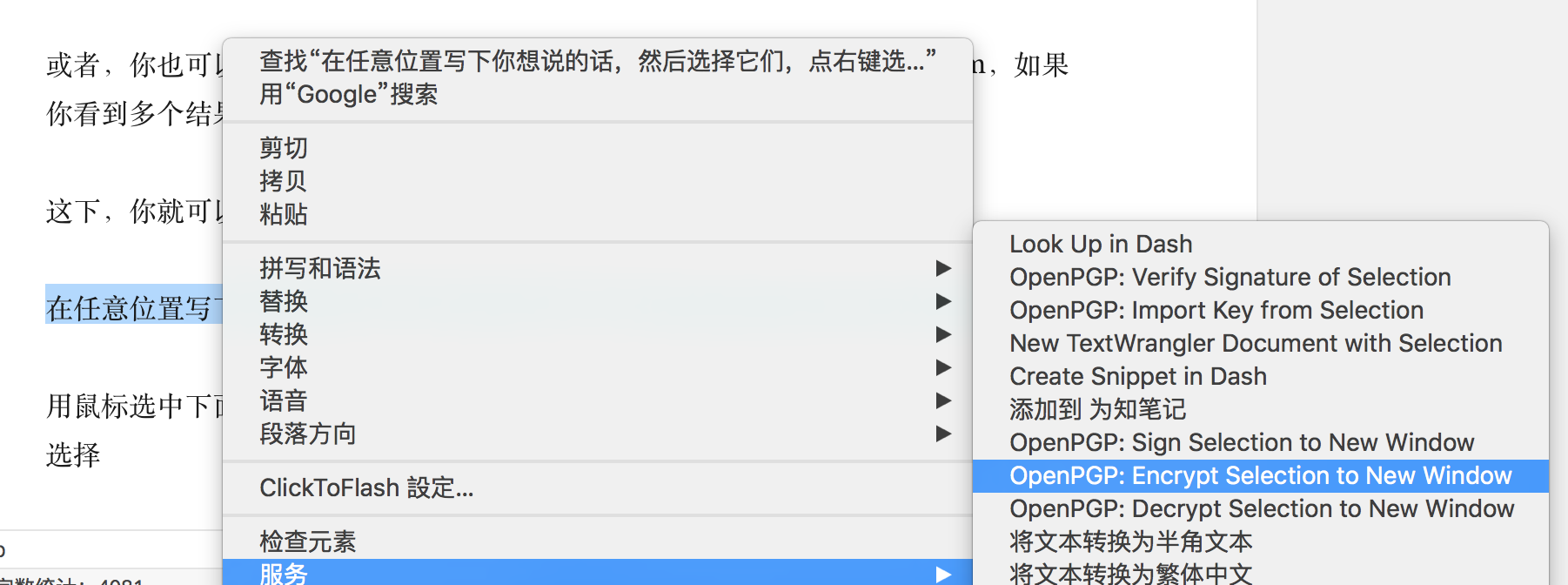
Write down what you want to say in any position,, And then select them,In new window right click Select encryption!
In the pop-up window, select what you want to use public-key encryption-the General,Who do you want to see,Who encrypt to it! To test selected their own,Then a copy of the window comes out,You only need to copy the encrypted content and then sent to inside! (For example, QQ~ for example mail ~)
Same,Select encrypt information you see,Then select decrypt,Will be able to decrypt the ~ if you have to make sure this is sent to you--that content encrypted using your public key ~ you can not undo it!
Other,If you are in the TextWrangler This type of encryption and decryption in the editor,You mayCould not be foundRight-service--it doesn't matter,TextWrangler this menu in the menu bar,have Services This menu,Is it!
At last,Let us say a message,after all,This is the most common thing。For mail,Here I take ThunderBird As an example,,We click on the menu " Tools(T)–>Additional components(A) ”,From "Get Add-ons"Search Enigmail,select" Add to the Thunderbird(A)… ”,To install ThunderBird Enigmail plugin,It provides OpenPGP support。ThunderBird's security with PGP support,Not convenient to use。We use this plugin,More comfortable。
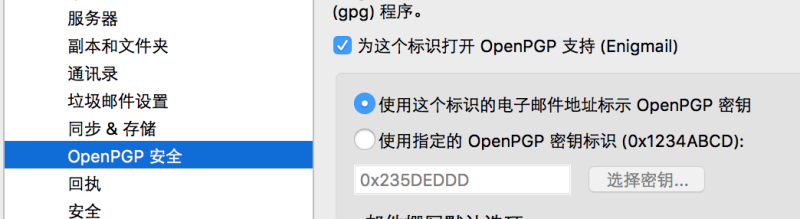
Then set during the installation wizard directly to。If you have multiple mailboxes and generates multiple keys,Then you need to enter the settings for the mailbox in the OpenPGPSafety Select "Use this to identify the email address signs OpenPGP keys”。
Now,You can compose a new message when trying to use encryption! If necessary,You can also check "Comes with my public key”;Other,If your recipient does not have a public key and you forced encryption,Plugin will prompt you and help you to automatically download one from a public key server ... ... Yes, sure,If you still can't find it. ... ... Will have to cancel the forced encryption to be sent!
If you receive an encrypted message,Only need to click on the page to decrypt,Then you can enter your private key password ~
Isn't it convenient?
Give it a try
At last,You have configured the service,Learn encryption,And also add my public key-now you can try to send me an emailEncryptionMail it! I will definitely get back to you yo ~
besides,Remember to use my public key encryption,Don't get me wrong I can't open it,besides,Remember that comes with your public key so that I can get back to you:)
Lomyr.Jo@gmail.com pocketed blog。
References
- GnuPG and message encryption
- Cryptography
- Pretty Good Privacy
- GPGTools
- The best PGP tutorial for Mac OS X, ever
- OpenPGP PGP GPG Difference
- The GNU Privacy Guard
Original article written by LogStudio:R0uter's Blog » Encryption and decryption - make your information more secure
Reproduced Please keep the source and description link:https://www.logcg.com/archives/1471.html
Comments