Some time ago the appleID theft uproar,I determined to return to prison upgraded 9.0. This is just great,Shadowsocks can not be used。This concerned me quite envious of Android phones……Use Surge let go Shadowsocks iOSRealize Scientific Internet。
In short,We still have to work hard in the VPN, right up and down iOS。Today's VPN has been certified almost,Because although they cryptographic security,Could not help but feature detection - Well,After all, this thing saysNot to conceal born。Cisco currently touches me there is a big father alive anyconnect,It is not how strong,But with too many businesses,Can not ban,and,It also has automatic disconnection connection,Many of the benefits of automatic diversion of domestic and foreign demand - the largest point:You do not need to jailbreak。
note:
I am usingDigital OceanThe VPS,Ubuntu 15.04 ,The whole configuration step is to side with the side of my record,It is entirely feasible,However, due to the complex system environment,Everyone is different,So when your specific operation may still need to be flexible to use!
0、Questions about PAC
We often say,Cisco's AnyConnect yesUnable to use PACof,Because of its different mechanism,Not the agent but the VPN,Therefore, the method used herein is the direct route entry number issued from the server - Because the client restrictions,We can not always issued a complete routing table (only 200 pieces),This is always the majority AnyConnect a heart disease。In short,In fact, there is another one way,For those who need a global vpn but want to distinguish the network business,Cisco still has a corresponding way。
That is to let go proxy server。?
That you have a demand of China as a pre-vps,And this vps use other tools such as Shadowsocks connected to your foreign vps,Then build ocserv in China vps,Then configure it pac file,Such ocserv will be based on your proxy strategies to achieve routing。In short,If you want to try this method,Please direct jump at the bottom of the page [Reference article] Section,“Venue Anyconnect VPN to use PAC smart shunt"This reference articles。
1、Configuration Environment
This step reference I wrote earlieran article- If you are new vps,Otherwise skip it -
2、Erection OpenConnectServer
2.1Download Source
See ocserv the latest version from here,You do not need to point to an FTP watching,Just replace the installation format link path on the line。For example, now the latest version is 0.10.8,Then you put the address written as: ftp://ftp.infradead.org/pub/ocserv/ocserv-0.10.8.tar.xz ,it is good,We now Download Source:
|
1 2 |
wget ftp://ftp.infradead.org/pub/ocserv/ocserv-0.10.8.tar.xz tar xvf ocserv-0.10.8.tar.xz |
2.2 Installation depends
Download extract good code,You need to install the dependencies,These are needed,Some are optional,Here we try to install all the dependencies,In case of future need it too! After all, it's ten trillion size。
|
1 2 3 4 |
sudo apt-get install build-essential pkg-config libgnutls28-dev libreadline-dev libseccomp-dev libwrap0-dev libnl-nf-3-dev liblz4-dev cd ocserv-0.10.8 ./configure |
If there is no problem,It can be installed,For example, here are my results so:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
ummary of build options: version: 0.10.8 Host type: x86_64-unknown-linux-gnu Install prefix: /usr/local Compiler: gcc CFlags: -g -O2 -Wall PAM auth backend: no Radius auth backend: no GSSAPI auth backend: no Anyconnect compat: yes TCP wrappers: yes systemd: no (socket activation) seccomp: yes Compression: yes LZ4 compression: no readline: yes libnl3: yes glibc (sha2crypt): yes local talloc: yes local protobuf-c: yes local PCL library: yes local libopts: yes local http-parser: yes |
2.3 Compile and install
Use the make command to compile and install:
|
1 2 3 |
make sudo make install |
3、配置 OpenConnectServer
3.1Prepare
Install Certificate Tools apt-get install gnutls-bin
|
1 2 3 4 5 |
cd ~ mkdir certificates cd certificates |
Create a directory named in this that.TMPL CA certificate template,Write the following statement:
|
1 2 3 4 5 6 7 8 |
cn = "Logcg.com" organization = "logcg.com" serial = 1 expiration_days = 3650 ca signing_key cert_signing_key crl_signing_key |
use certtool --generate-privkey --outfile that-key.estab CA key generation;
use certtool --generate-self-signed --load-privkey that-key.estab --template that.TMPL --outfile that-cert.estab Generated CA certificate;
Then we generate the server certificate,Note here that cn items must correspond to your server's domain name or IP,Template name is server.TMPL ,Follows:
|
1 2 3 4 5 6 |
cn = "Your hostname or IP" organization = "logcg.com" expiration_days = 3650 signing_key encryption_key tls_www_server |
use certtool --generate-privkey --outfile server-key.estab Generate the key;
use certtool --generate-certificate --load-privkey server-key.estab --load-that-certificate that-cert.estab --load-that-privkey that-key.estab --template server.TMPL --outfile server-cert.estab Generate server certificates;
The certificate is moved to the right place:
|
1 2 3 |
cp ca-cert.pem /etc/ssl/private/my-ca-cert.pem cp server-cert.pem /etc/ssl/private/my-server-cert.pem cp server-key.pem /etc/ssl/private/my-server-key.pem |
3.2 Prepare the configuration file
We put the configuration file default location ocserv read:
|
1 2 3 |
mkdir /etc/ocserv cd ~/ocserv-0.10.8 cp doc/sample.config /etc/ocserv/ocserv.conf |
The configuration file can referenceOfficial HandbookTo write,But here we focus on to ensure that the following entries are correct:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
# 登陆方式,目前先用密码登录 auth = "plain[/etc/ocserv/ocpasswd]" # 允许同时连接的客户端数量 max-clients = 4 # 限制同一客户端的并行登陆数量 max-same-clients = 2 # 服务监听的IP(服务器IP,可不设置) listen-host = 1.2.3.4 # 服务监听的TCP/UDP端口(选择你喜欢的数字) tcp-port = 9000 udp-port = 9001 # 自动优化VPN的网络性能 try-mtu-discovery = true # 确保服务器正确读取用户证书(后面会用到用户证书) cert-user-oid = 2.5.4.3 # 服务器证书与密钥 server-cert = /etc/ssl/private/my-server-cert.pem server-key = /etc/ssl/private/my-server-key.pem # 客户端连上vpn后使用的dns dns = 8.8.8.8 dns = 8.8.4.4 # 注释掉所有的route,让服务器成为gateway #route = 192.168.1.0/255.255.255.0 # 启用cisco客户端兼容性支持 cisco-client-compat = true |
3.3 Test Server
Now,Since we can test the server,Use the command to create a test account:
|
1 2 3 |
root@iZ289z55gmrZ:~/ocserv-0.10.8# ocpasswd -c /etc/ocserv/ocpasswd test Enter password: Re-enter password: |
Also if you are using Ubuntu system,Then you can follow what I wroteThis articleTo open the NAT forwarding;
use iptables -t nat -L To verify the transponder is turned on success:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
root@iZ289z55gmrZ:~# iptables -L -t nat Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain INPUT (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination MASQUERADE all -- 192.168.1.0/24 anywhere |
Then,We can use ocserv -f -d 1 Command to start the next service it!
Open the Cisco Anyconnect on your mobile phone to create a VPN,Add the server's IP is your vps IP:port
All right,If you see the following information,The server should be able to have a normal operation:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
root@iZ289z55gmrZ:~# ocserv -f -d 1 Parsing plain auth method subconfig using legacy format Setting 'plain' as primary authentication method listening (TCP) on 0.0.0.0:110... listening (UDP) on 0.0.0.0:9000... ocserv[16104]: main: initialized ocserv 0.10.8 ocserv[16105]: sec-mod: reading supplemental config from files ocserv[16105]: sec-mod: sec-mod initialized (socket: /var/run/ocserv-socket.16104) ocserv[16109]: GnuTLS error (at worker-vpn.c:468): A TLS fatal alert has been received.: Unknown certificate ocserv[16104]: main: 60.0.14.48:9890 user disconnected ocserv[16105]: sec-mod: using 'plain' authentication to authenticate user (session: FXS0l) ocserv[16104]: main: 60.0.14.48:36627 user disconnected ocserv[16105]: sec-mod: initiating session for user 'test' (session: FXS0l) ocserv[16104]: main[test]: 60.0.14.48:9663 new user session ocserv[16104]: main[test]: 60.0.14.48:9663 user logged in ocserv[16104]: main: 60.0.14.48:46429 user disconnected ocserv[16104]: main[test]: 60.0.14.48:9663 user disconnected ocserv[16105]: sec-mod: temporarily closing session for test (session: FXS0l) ocserv[16105]: sec-mod: initiating session for user 'test' (session: FXS0l)ocserv[16104]: main[test]: 60.0.14.48:38135 new user session ocserv[16104]: main[test]: 60.0.14.48:38135 user logged in |
3.4 Optimization OpenConnectServer
All right,Since the server is ready to run up,Then we can optimize it,First of all,Write a script to start - after all,,Are not using debug mode every time you start is not it?
If you're like me using Ubuntu 15.04 Instead Older,Then you need to refer toThis articleTo retrieve what upstart can use the script below。
|
1 2 3 4 5 |
cd /etc/init.d ln -s /lib/init/upstart-job ocserv cd /etc/init vi ocserv.conf |
Write the following script in the configuration file:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
#!upstart description "OpenConnect Server" start on runlevel [2345] stop on runlevel [06] respawn respawn limit 20 5 script exec start-stop-daemon --start --pidfile /var/run/ocserv.pid --exec /usr/local/sbin/ocserv -- -f >> /dev/null 2>&1 end script |
Such,We can use service ocserv start and service ocserv stopTo control the service。
3.5 Create a client certificate,Enter the old password province
|
1 2 |
cd ~/certificates/ vi user.tmpl |
Write the following:
|
1 2 3 4 5 |
cn = "some random name" unit = "some random unit" expiration_days = 365 signing_key tls_www_client |
|
1 2 3 4 5 6 7 |
//User密钥 certtool --generate-privkey --outfile user-key.pem //User证书 certtool --generate-certificate --load-privkey user-key.pem --load-ca-certificate ca-cert.pem --load-ca-privkey ca-key.pem --template user.tmpl --outfile user-cert.pem |
PKCS12 certificates and keys into a format,Good import Anyconnect:
|
1 |
certtool --to-p12 --load-privkey user-key.pem --pkcs-cipher 3des-pkcs12 --load-certificate user-cert.pem --outfile user.p12 --outder |
During the certificate will ask you to enter the name and password。
Then you need to put this into place a certificate that can be accessed directly,Then the URL user.p12 file into AnyConnect,Specific location section under the Diagnostics tab page Certificates,After successfully imported,The Advanced Settings section of the VPN settings corresponding certificate section,This certificate to import。
Now,In order for the server to recognize this certificate,Let's modify the configuration:
|
1 2 3 4 5 6 7 8 9 10 |
vi /etc/ocserv/ocserv.conf # 改为证书登陆,注释掉原来的登陆模式 auth = "certificate" # 证书认证不支持这个选项,注释掉这行 #listen-clear-file = /var/run/ocserv-conn.socket # 启用证书验证 ca-cert = /etc/ssl/private/my-ca-cert.pem |
Such,We use service ocserv start To start it you can!
4、Smart shunt
All right,usually,If you are a stable and does not slow the speed of foreign vps,Well, now you can start to enjoy life! but,Our mission has not ended with,Manual switching can not say is smart,We use the ready-made。
https://github.com/don-johnny/anyconnect-routes/blob/master/routes
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 |
# Dropbox route = 108.160.0.0/255.255.0.0 route = 199.47.0.0/255.255.0.0 route = 205.189.0.0/255.255.0.0 # Facebook route = 58.26.0.0/255.255.0.0 route = 210.149.0.0/255.255.0.0 route = 31.13.0.0/255.255.0.0 route = 66.220.0.0/255.255.0.0 route = 69.63.0.0/255.255.0.0 route = 69.171.0.0/255.255.0.0 route = 74.119.0.0/255.255.0.0 route = 173.252.0.0/255.255.0.0 route = 199.201.0.0/255.255.0.0 route = 204.15.0.0/255.255.0.0 route = 1.9.0.0/255.255.0.0 # Github route = 192.30.0.0/255.255.0.0 route = 23.235.0.0/255.255.0.0 route = 199.27.0.0/255.255.0.0 route = 104.156.0.0/255.255.0.0 # Google route = 8.6.0.0/255.255.0.0 route = 8.8.0.0/255.255.0.0 route = 8.15.0.0/255.255.0.0 route = 8.34.0.0/255.255.0.0 route = 8.35.0.0/255.255.0.0 route = 23.236.0.0/255.255.0.0 route = 23.251.0.0/255.255.0.0 route = 64.9.0.0/255.255.0.0 route = 64.233.0.0/255.255.0.0 route = 66.102.0.0/255.255.0.0 route = 66.249.0.0/255.255.0.0 route = 70.32.0.0/255.255.0.0 route = 72.14.0.0/255.255.0.0 route = 74.125.0.0/255.255.0.0 route = 104.132.0.0/255.252.0.0 route = 104.154.0.0/255.254.0.0 route = 104.196.0.0/255.252.0.0 route = 107.167.0.0/255.255.0.0 route = 107.178.0.0/255.255.0.0 route = 108.59.0.0/255.255.0.0 route = 108.170.0.0/255.255.0.0 route = 108.177.0.0/255.255.0.0 route = 130.211.0.0/255.255.0.0 route = 142.250.0.0/255.254.0.0 route = 146.148.0.0/255.255.0.0 route = 162.216.0.0/255.255.0.0 route = 162.222.0.0/255.255.0.0 route = 172.217.0.0/255.255.0.0 route = 172.253.0.0/255.255.0.0 route = 173.194.0.0/255.255.0.0 route = 173.255.0.0/255.255.0.0 route = 192.158.0.0/255.255.0.0 route = 192.178.0.0/255.254.0.0 route = 199.192.0.0/255.255.0.0 route = 199.223.0.0/255.255.0.0 route = 207.223.0.0/255.255.0.0 route = 209.85.0.0/255.255.0.0 route = 216.58.0.0/255.255.0.0 route = 216.239.0.0/255.255.0.0 #google ext 2015-08-27 route = 111.168.0.0/255.255.0.0 # Twitter route = 8.25.0.0/255.255.0.0 route = 192.133.0.0/255.255.0.0 route = 199.16.0.0/255.255.0.0 route = 192.229.0.0/255.255.0.0 route = 104.244.0.0/255.255.0.0 route = 199.59.0.0/255.255.0.0 route = 199.96.0.0/255.255.0.0 # Wikimedia route = 91.198.0.0/255.255.0.0 route = 185.15.0.0/255.255.0.0 route = 198.35.0.0/255.255.0.0 route = 198.73.0.0/255.255.0.0 route = 208.80.0.0/255.255.0.0 # instagram route = 54.0.0.0/255.0.0.0 route = 52.0.0.0/255.0.0.0 route = 72.246.0.0/255.255.0.0 route = 23.32.0.0/255.255.0.0 route = 125.56.0.0/255.255.0.0 #1024 route = 162.159.246.97/255.255.255.255 #Linn Radio route = 89.16.0.0/255.255.0.0 #Quaro route = 192.33.31.60/255.255.255.255 route = 103.243.12.60/255.255.255.255 #www.flinto.com route = 103.245.0.0/255.255.0.0 #TELEGRAM route = 91.108.0.0/255.255.0.0 route = 149.154.0.0/255.255.0.0 #vfsglobal.com route = 210.210.0.0/255.255.0.0 |
But I did not write the whole,He wrote only part of the inside - I mainly brush push -
All right,Right here!
Reference article:
Toss notes:Erection OpenConnect Server for iPhone provides smoother network life
Anyconnect VPN to use PAC smart shunt
Original article written by LogStudio:R0uter's Blog » Ocserv build server using Cisco Anyconnect
Reproduced Please keep the source and description link:https://www.logcg.com/archives/1343.html
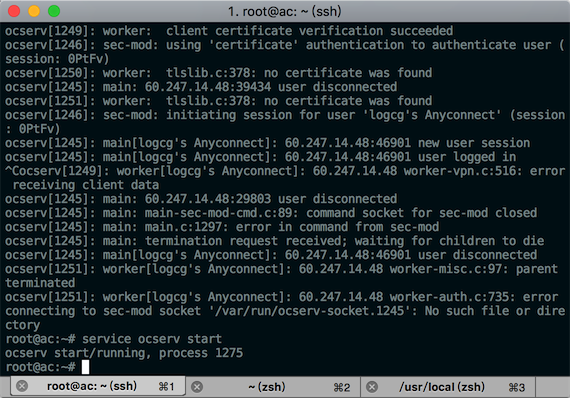
ocserv -f -d 1 start service can be used normally。After running service ocserv start,Enter IP to connect to the server,After clicking continue,It says can't connect to server。what reason?
Can you ping the server?
Try curl? usually,gfw will block and block you as soon as you connect.,Try changing to a random port,And use a foreign server to run the client and connect to confirm whether it is gfw or the service is not paired.。
Other,Make sure your port is accessible,such as server firewall,And if you use cloud services,Usually the platform itself has a default firewall,Maybe only port 22 is opened,Also open it。
What is the difference between ocserv -f -d 1 and service ocserv start?
ocserv -f -d 1 start,Mobile phone Cisco Anyconnect can log in with account and password,Can access external networks such as Google。It means there is no problem with the firewall port or anything like that.。
Switch to service ocserv start start,connect to the server,After clicking continue,It says can't connect to server。
Unknown,It depends on the script code.,Maybe the script of service lacks some necessary firewall configuration。
Hello,would like to ask。
After setting up the service with reference to your article,AnyConnect can connect,But after connecting, I can't access google.
i tried
telnet ip port and nc commands tested TCP and UDP
iptables -t nat -L The result is also consistent with yours
net.ipv4.ip_forward=1 no comment
can you give me an idea,Thank you
First look at where your server room is,let's say it's in the west,Then try it first, for example, if you can visit my blog,This way we can determine if you are dns polluted or not,dns pollution goes both ways,Not only for domestic,also for foreign。
Then make sure to curl google on the server,Make sure the server itself is connected
You telnet and the ip is through,It means that there is no problem with accessing the server locally,Then I guess it is very likely to be a problem with DNS resolution (especially if only blocked websites such as Google cannot be opened,Start with this
In addition, tools such as wireguard may be much better than anyconnect now,After all, the latter should have been recognized and blocked by gfw by now…………
my server,Use of IPSec that has been deployed,The server itself is fine。
But IPSec has poor support for windows,Registry needs to be modified、DNS and group policy issues,I learned about ocserv a few days ago and wanted to try it。
Who knew that another wireguard appeared,still narrow vision,First time hearing about this
Based on my experience deploying this thing back in the day,gfw is see one seal one,Maybe your server was fine before,but he got this,started to interfere。That's why I gave up on it so quickly,it's just encrypted,not confused,It is generally difficult to live long。
wireguard is relatively new,It's small code size but high performance,send packets using UDP,But in some operators there may be restrictions on UDP,The effect is not necessarily the best,But definitely better than AnyConnect。
Which hello,Is there centos installation method it?
Hello there,I would like to know,anyconnect can set the global routing,Always have a little trouble updating
The default is the global routing
Bloggers seek advice finally make a mistake when turning back the next question should be out here some of these libraries are to me how to add them to the build path go? Thank you
local talloc: no
local protobuf-c: no
local PCL library: no
local libopts: no
local http-parser: no
These libraries can be used to install the apt-get。
Get yourself in trouble before the whole library is based on the Chinese online tutorial patchwork….barley
See the next official readme finally get
https://tyr.gift/anyconnect-pac.html
anyconnect can also be used for automatic proxy pac,Rather than routing table
I go to Le! Turned out to be true! ---- Well I neglected friends,Really I do not even own to explore some - what I'll update the article。
https://github.com/CNMan/ocserv-cn-no-route
This no-route better than you are now
Thank you to answer!
Another problem is opening NAT forwarding https://www.logcg.com/archives/993.html
Adding forwarding port forwarding entries and open content under can copy it? If you need to change I do not know what to fill,Do not know。。。
I beg you to answer,Thank you!
Uh,Theoretically according to your port is able to copy - at least this is on my vps command。if not,You think of ways it ~
R0uter:
Hello there!
I am more layman,Ask you something,I also use the VPS Digital Ocean,Ubuntu 15.04 ,$ 5 monthly fee that paragraph,Before you follow the http://www.chedanji.com/ubuntu-shadowsocks/ this post deployed Shadowsocks , Android phones and PC can be turned,As you are now ready to build this masterpiece Cisco Anyconnect server,I can operate it? Previous Shadowsocks will conflict?
Hope reply,Thank you!
do not worry,Casually with,My vps now both ran without any problems! The only caveat is that:To avoid port conflicts。Just keep this in mind to ok。but,ac in my speed is not ye,I'm ready to unload it。Recommend the latest surge!